📑 Text Obfuscator - Hide data from web scrapers
The purpose of this online tool is to take any piece of text and convert it to a JavaScript expression which evaluates back to that original text. This strategy is useful when trying to protect data from being scraped by automated bots. It works because the resulting code produced by the obfuscator will appear as gibberish script code inside HTML source code (which basic scrapers will have a hard time parsing), but your web-browser will be able to render it back to the original data with no problems.
This method of data protection is far from bulletproof, given that headless scrapers are capable of executing JavaScript code, and will thus be able to see the complete text as it would appear in a real web-browser. Obfuscation is an example of security through obscurity, and an experienced scraper with enough resources will be able to defeat it. But at the very least, we are making things much more difficult for them, and in some cases that is enough.
Start by typing the data you want to protect in the text-field below:
This same obfuscation strategy is being used on this very site on our proxy servers list page, where we publish the list of IP addresses on the Internet that are open for public use. A lot of the applications out there would like to make use of that data, and so they built scrapers that periodically scan that page for proxies that are then imported and used by those services. We want to prevent them from doing that if for no other reason other than to not have that page receive thousands of requests per minute.
Originally the idea was to display all IP addresses as images:
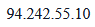 However, that prevents users from being able to
copy and paste those addresses into their application, and instead they would have had to type those numbers in
manually.
However, that prevents users from being able to
copy and paste those addresses into their application, and instead they would have had to type those numbers in
manually.
Another idea was to make users solve captcha challenges if they visit that page too many times. But captchas are
annoying, and it would not have stopped scrapers that do not scrape that page too often.
Obfuscating each IP address as JavaScript code was the least intrusive solution. So right now when you visit our proxy list page, all the data on it is plainly visible when viewing via web-browser. However, if you were to right-click and view source code of that page, you will not see any IP addresses in plain text, but instead see code snippets like this:
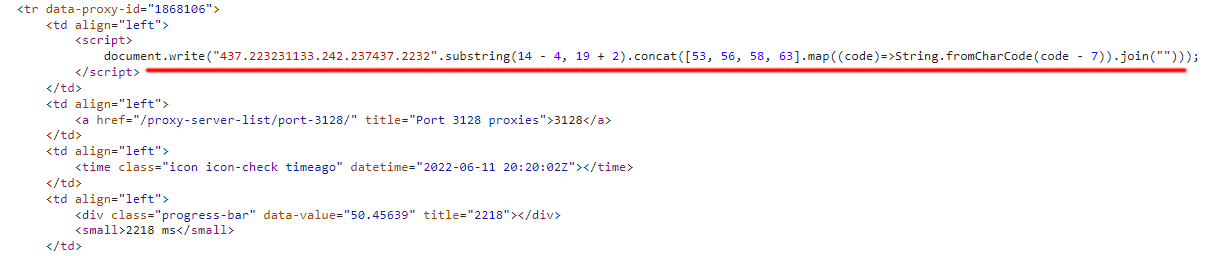
Much harder to decode for scrapers!
Email Obfuscation - Prevent Email Scraping
This same strategy of obfuscating text with JavaScript code, can also be used to obfuscate email addresses against email scrapers that typically look for emails embedded as plain text like the example below which is very easy to parse out:
<p>Send us your questions and comments - <a href="mailto:feedback@amazon.com">feedback@amazon.com</a>
That same snippet with email portion "encrypted", will make it much harder for web-scrapers to extract, and would will look something like this:
<p>Send us your questions and comments -
<script>document.write(atob("PGEgaA==").concat([213,200,201,160].map((c) => String.fromCharCode(c - 99)).join("")).concat("ia\"\"maii".substring(3,7)).concat("otlto:o".substring(2,6)).concat([122,121,121,120].map((c) => String.fromCharCode(c - 20)).join("")).concat([138,137,139,147].map((c) => String.fromCharCode(c - 40)).join("")).concat("a@a@amaa@a".substring(3,7)).concat(atob("em9uLg==")).concat(atob("Y29tIg==")).concat("eef>".split("").reverse().join("")).concat(atob("ZGJhYw==")).concat([182,139,172,184].map((c) => String.fromCharCode(c - 75)).join("")).concat("noza".split("").reverse().join("")).concat("moc.".split("").reverse().join("")).concat(">a/<".split("").reverse().join("")));</script>
</p>
JavaScript library
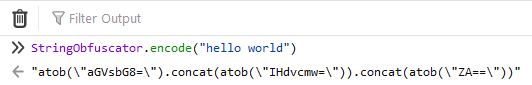
Use the same library used on this page for your own purposes:
StringObfuscator.js
Rest API
Use this from another application. No API keys needed. You are limited to about a thousand requests per day.
curl -X POST https://api.proxynova.com/obfuscate -d "hello world"
"hel".repeat(3).substring(6).concat("dlrow ol".split("").reverse().join(""))
 United States (838)
United States (838) Convert any tweet to static image
Convert any tweet to static image
 Send email to anyone anonymously
Send email to anyone anonymously
 Check Alexa Rank for sites
Check Alexa Rank for sites